| xshell中抓包 | 您所在的位置:网站首页 › python抓包工具 丢包问题 › xshell中抓包 |
xshell中抓包
|
1。查看我们xshell是否有抓包工具 输入命令tcpdump。如果有图下所示:就证明安装有(一般都会自带安装有)
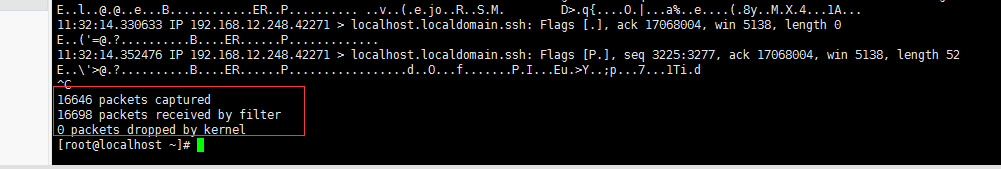
2.以下命令进行抓包 tcpdump -i ens192 host 192.168.0.66 -s 1024 -A (这个是抓ip的包) tcpdump -i ens192 port 8080 -s 1024 -A (这个是抓port的) tcpdump -i ens192 host 192.168.0.66 and port 20250 -s 1024 -A (指定服务器和端口号) 3.以下是抓到的包
其中“captured”的计数指的是应用层捕获到的数据,“received by filter”和“dropped by kernel”的计数由内核维护,应用层通过getsockopt来获取。收到一个包,“received by filter”会加1,如果sock的接收buffer被填满时,则把这个数据包丢弃,将“dropped by kernel”加1。 if (atomic_read(&sk->sk_rmem_alloc) + skb->truesize >= (unsigned)sk->sk_rcvbuf){ spin_lock(&sk->sk_receive_queue.lock); po->stats.tp_drops++; spin_unlock(&sk->sk_receive_queue.lock); } 通过调节/proc/sys/net/core/rmem_default和/proc/sys/net/core/rmem_max能够改变sk_rcvbuf的大小。 正常“captured”加上“dropped by kernel”应该等于“received by filter”的大小,有的时候出现不等的情况应该是还有一些数据包在sk_rcvbuf中,还没有被应用层收到的原因。 丢包原因:经过google以及分析,造成这种丢包的原因是由于libcap抓到包后,tcpdump上层没有及时的取出,导致libcap缓冲区溢出,从而覆盖了未处理包,此处即显示为dropped by kernel,注意,这里的kernel并不是说是被linux内核抛弃的,而是被tcpdump的内核,即libcap抛弃掉的 解决方法: 根据以上分析,可以通过改善tcpdump上层的处理效率来减少丢包率,下面的几步根据需要选用,每一步都能减少一定的丢包率 1. 最小化抓取过滤范围,即通过指定网卡,端口,包流向,包大小减少包数量 2. 添加-n参数,禁止反向域名解析 3. 添加-B参数,加大OS capture buffer size 4. 指定-s参数, 最好小于1000 5. 将数据包输出到cap文件 6. 用sysctl修改SO_REVBUF参数,增加libcap缓冲区长度:/proc/sys/net/core/rmem_default和/proc/sys/net/core/rmem_ma -B buffer_sizeSet the operating system capture buffer size to buffer_size, in units of KiB (1024 bytes).-nDon't convert addresses (i.e., host addresses, port numbers, etc.) to names.-s snaplen--snapshot-length=snaplenSnarf snaplen bytes of data from each packet rather than the default of 65535 bytes. Packets truncated because of a limited snapshot are indicated in the output with ``[|proto]'', where proto is the name of the protocol level at which the truncation has occurred. Note that taking larger snapshots both increases the amount of time it takes to process packets and, effectively, decreases the amount of packet buffering. This may cause packets to be lost. You should limit snaplen to the smallest number that will capture the protocol information you're interested in. Setting snaplen to 0 sets it to the default of 65535, for backwards compatibility with recent older versions of tcpdump.
|
【本文地址】